Configure Windows Defender Exploit Guard (WDEG) in Windows 11/10
Windows Defender Exploit Guard runs all the security benefits necessary to keep intrusion threats at bay. A characteristic feature of this tool is 'Exploit Protection'. It automatically applies to many exploit mitigation techniques. This capability can be tested within the Windows Defender Security Center nether App & browser control > Exploit protection. By accessing the Exploit protection settings, you can command system-wide settings and program-specific overrides. Let us learn how to configure, and manage Windows systems and application exploit mitigations using Windows Defender Exploit Guard (WDEG).
Windows Defender Exploit Guard (WDEG)
Exploit Guard can be found in the Security Analytics dashboard of the Windows Defender ATP console. Its primary function is to enable enterprises to view how the feature is configured across their device and to drive compliance with recommendations based on best practice security configurations.
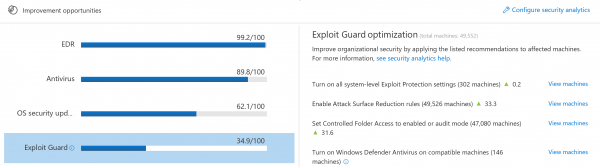
You can configure Windows Exploit Guard for,
- Assault surface reduction
- Exploit Protection
- Network Protection
- Controlled Folder Access
All the Windows Defender Exploit Baby-sit components can exist readily managed by
- Group Policy (GP)
- System Center Configuration Manager (SCCM)
- Mobile Device Management (MDM) such as Microsoft Intune.
These components can run in both Inspect and Block modes. If whatever instance of malicious behavior is observed, when Block mode is enabled, Windows Defender Exploit Guard automatically blocks the result from occurring in existent-time.
By default, Cake events for Assail Surface Reduction, Controlled folder admission, and Network Protection instantly display a toast notification in real-time as well as an event log that tin be centrally viewed by security operations personnel in the Windows Defender Advanced Threat Protection (WD ATP) panel.
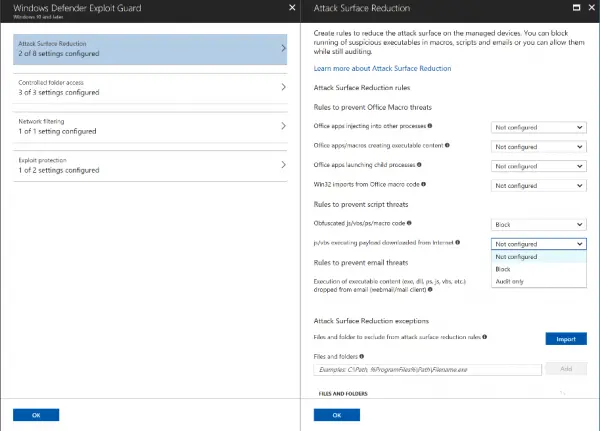
The Inspect Mode detects the possibility of an occurrence of an outcome if it would accept occurred and conveys that information to the event log and WD ATP panel. This helps enterprises customers to evaluate how a rule or feature within Windows Defender Exploit Guard would perform in their enterprise which in turn helps in the decision-making process of determining whether exclusions are required to gear up.
Configure Windows Defender Exploit Guard for mitigations
While but a few mitigations tin can be applied at the operating system level. All mitigations tin be configured for individual apps.
As always, y'all can set value for each of the mitigations to either on/off, or to their default value.
The default values are always specified in brackets at the 'Utilize default' option for each mitigation. In the screenshot provided below, the default for Information Execution Prevention is "On".
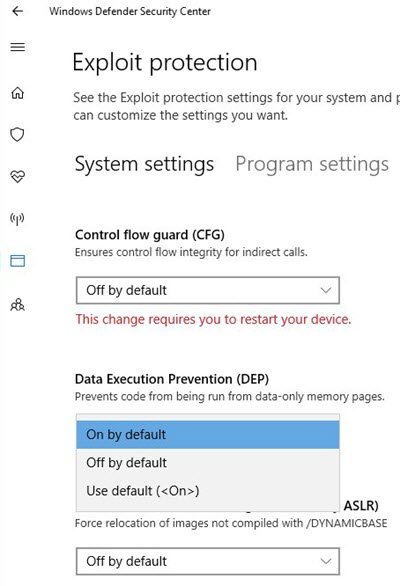
By and large, the employ of default configuration for each of the mitigation settings is advised for offering a base level of protection, especially for daily usage by home users. For Enterprise deployments, it is advisable to consider the protection features suitable to individual needs.
The all-time part nigh using Windows Defender Exploit Guard is that you can take advantage of its settings even if y'all're running third-party antivirus.
Source: Technet.

Source: https://www.thewindowsclub.com/windows-defender-exploit-guard
Posted by: comptoneusive.blogspot.com


0 Response to "Configure Windows Defender Exploit Guard (WDEG) in Windows 11/10"
Post a Comment